Pohlig–Hellman algorithm
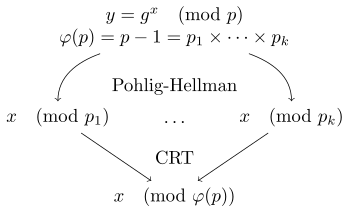
In number theory, the Pohlig–Hellman algorithm sometimes credited as the Silver–Pohlig–Hellman algorithm[1] is a special-purpose algorithm for computing discrete logarithms in a multiplicative group whose order is a smooth integer.
The algorithm was discovered by Roland Silver, but first published by Stephen Pohlig and Martin Hellman (independent of Silver).
We will explain the algorithm as it applies to the group Z*p consisting of all the elements of Zp which are coprime to p, and leave it to the advanced reader to extend the algorithm to other groups by using Lagrange's theorem.
- Input Integers p, g, e.
- Output An Integer x, such that e ≡ gx (mod p) (if one exists).
- Determine the prime factorization of the order of the group :
(All the pi are considered small since the group order is smooth.) - From the Chinese remainder theorem it will be sufficient to determine the values of x modulo each prime power dividing the group order. Suppose for illustration that p1 divides this order but p12 does not. Then we need to determine x mod p1, that is, we need to know the ending coefficient b1 in the base-p1 expansion of x, i.e. in the expansion x = a1 p1 + b1. We can find the value of b1 by examining all the possible values between 0 and p1-1. (We may also use a faster algorithm such as baby-step giant-step when the order of the group is prime.[2]) The key behind the examination is that:
(using Euler's theorem). With everything else now known, we may try each value of b1 to see which makes the equation be true. If , then there is exactly one b1, and that b1 is the value of x modulo p1. (An exception arises if since then the order of g is less than φ(p). The conclusion in this case depends on the value of on the left: if this quantity is not 1, then no solution x exists; if instead this quantity is also equal to 1, there will be more than one solution for x less than φ(p), but since we are attempting to return only one solution x, we may use b1=0.) - The same operation is now performed for p2 through pn.
A minor modification is needed where a prime number is repeated. Suppose we are seeing pi for the (k + 1)st time. Then we already know ci in the equation x = ai pik+1 + bi pik + ci, and we find either bi or ci the same way as before, depending on whether . - With all the bi known, we have enough simultaneous congruences to determine x using the Chinese remainder theorem.
- Determine the prime factorization of the order of the group :
Complexity
The worst-case time complexity of the Pohlig–Hellman algorithm is for a group of order n, but it is more efficient if the order is smooth. Specifically, if is the prime factorization of n, then the complexity can be stated as .[3]
Notes
- ↑ Mollin 2006, pg. 344
- ↑ Menezes, et. al 1997, pg. 109
- ↑ Menezes, et. al 1997, pg. 108
References
- Mollin, Richard (2006-09-18). An Introduction To Cryptography (2nd ed.). Chapman and Hall/CRC. p. 344. ISBN 978-1-58488-618-1.
- S. Pohlig and M. Hellman (1978). "An Improved Algorithm for Computing Logarithms over GF(p) and its Cryptographic Significance" (PDF). IEEE Transactions on Information Theory (24): 106–110.
- Menezes, Alfred J.; van Oorschot, Paul C.; Vanstone, Scott A. (1997). "Number-Theoretic Reference Problems" (PDF). Handbook of Applied Cryptography. CRC Press. pp. 107–109. ISBN 0-8493-8523-7.